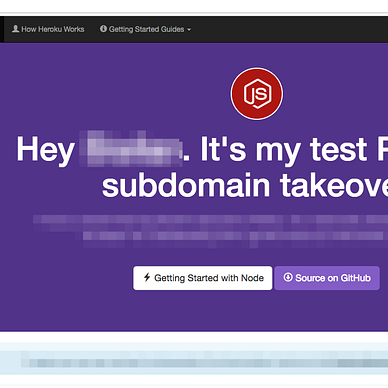
Subdomain Takeover guides, methodology and exploit POCs
Another day in Bug Bounty journey, today I learned about Subdomain TakeOver vulnerability.
To sum it up, I’ll explain the cause, exploitation methodology and preventive measures.
Subdomain TakeOver
Cause:
- A subdomain takeover happens when a subdomain points to an unused or misconfigured third-party service, and an attacker claims the resource.
- The attacker can claim the abandoned resource (e.g., register the same service) and gain control of the subdomain.
Exploitation Methodology:
- Discovery: Attackers identify subdomains pointing to inactive third-party services using tools like dig and nslookup that allows them their CNAME.
- Claiming: They register the same service (e.g., an AWS S3 bucket or Github Pages) to gain control.
- Exploitation: The attacker uploads malicious content, making the subdomain appear legitimate.
Preventive Measures (from GPT):
- Check DNS records regularly and remove unused subdomains.
- Verify subdomain ownership to ensure control over linked resources.
- Use monitoring tools to detect orphaned subdomains.
- Avoid wildcard DNS records unless necessary.
These measures help prevent subdomain takeover risks.
How to look for this vuln…?
Well, I prefer to keep a separate list of all the subdomains that throws a 404 error during the initial subdomain enumeration stage.
This allows me to have a list of subdomains that I can primarily check for Subdomain Takeovers.
Presence of all the 404s indicate that there used to be a service this was redirected to which is no longer present, hence we can register in its place and takeover the subdomain.
For reference, there’s a lot of articles, videos and reports I read which I’ll link below.
YouTube Videos :
Medium Articles :